Security in Custom Software Development: Best Practices
Introduction In today’s digital landscape, security is not just an additional layer; it is the foundation upon which all software solutions must be built. This is especially t...

Introduction
In today’s digital landscape, security is not just an additional layer; it is the foundation upon which all software solutions must be built. This is especially true for custom software development, where unique business needs require customised applications. However, with customisation comes the responsibility to ensure that security is built into every stage of development.
This article will explore the importance of integrating robust security in custom software development and provide best practices for protecting data, ensuring proper access controls, and minimising vulnerabilities.
Why Security in Custom Software Development is Critical
Custom software is developed specifically for the unique requirements of an organisation, meaning it often handles sensitive business transactions, confidential information, and personal data. The consequences of a security breach are serious, ranging from financial losses to reputational damage and legal consequences. Therefore, developers must integrate security measures in advance to protect both the business and its customers.
Unlike off-the-shelf software, where certain security protocols are standard, custom solutions require a customised security framework that matches the functionality of the software and the needs of the business.

Security in Custom Software Development: Core Practices
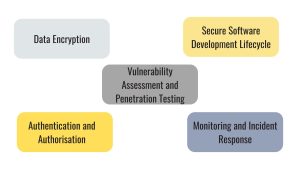
1. Data Encryption
Data encryption is one of the most fundamental security practices. It ensures that even if data is intercepted, it remains unreadable to unauthorised parties. Encryption should be used both in transit and at rest. Here’s how.
- Data encryption at rest: This protects data stored on servers or databases. Sensitive information, such as personally identifiable information (PII) or financial data, should always be encrypted, even when it is not being actively accessed.
- Data encryption in transit: When data is sent over a network, it is extremely vulnerable to interception. Using protocols such as Transport Layer Security (TLS) helps ensure that data is encrypted during transmission between the client and server.
To further strengthen encryption, use strong algorithms such as AES (Advanced Encryption Standard) with a key length of 256 bits. Using hashing algorithms to store passwords, such as SHA-256, also adds another layer of protection.
2. Authentication and Authorisation
A strong authentication and authorisation system is the foundation of secure user-facing software. These methods ensure that users are who they say they are and that they only have access to the information and resources required for their role.
- Authentication: This involves verifying the identity of users before granting access to the system. Multi-factor authentication (MFA) is a best practice in modern software development. It combines what the user knows (password), what they have (token or device), and who they are (biometric authentication) to prove their identity.
- Authorisation: Authorisation ensures that once authenticated, users only have access to the parts of the system that are relevant to them. Implementing role-based access control (RBAC) is essential, where users are assigned roles that determine their permissions within the application. Least privilege access should also be ensured, meaning users are given the minimum level of access necessary to complete their tasks.
3. Vulnerability Assessment and Penetration Testing
One of the key aspects of secure software development is identifying and eliminating potential vulnerabilities before they can be exploited. Vulnerability assessment and penetration testing are two strategies that ensure the security of a software system.
- Vulnerability assessment: This process involves scanning the software for potential security risks, such as outdated libraries, misconfigurations, or insecure coding practices. Automated tools can help detect common vulnerabilities, such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
- Penetration testing: Penetration testing simulates real-world attacks on the software to find vulnerabilities that can be exploited. This process goes beyond vulnerability scanning and involves experienced security testers attempting to break into the system. Penetration tests performed regularly are critical to identifying new vulnerabilities, especially as the software evolves and new features are added.
4. Secure Software Development Lifecycle (SDLC)
Security should be built in throughout the software development life cycle (SDLC). From the initial design phase to deployment, security considerations should guide every decision.
- Design Phase: Security begins during the design phase with threat modelling. Developers should anticipate potential attack vectors and design the system to mitigate these risks. Security should never be an afterthought; it should be a core part of the software architecture.
- Development Phase: During development, writing secure code is essential. Developers should follow secure coding standards such as OWASP Secure Coding Practices. In addition, code reviews should be conducted to identify and fix security issues early. Using automated static analysis tools can also help detect potential security flaws before they reach production.
- Testing and Deployment: In addition to functional testing, security testing should be performed during the software development process. Techniques such as fuzzy sampling testing, which involves sending random or invalid inputs to the software to test for failures or vulnerabilities, should be part of the test suite.
Once the software is deployed, it is equally important to secure the environment in which it runs. Server, database, and API configurations should comply with security best practices, including firewall rules, access control, and encryption protocols.
5. Monitoring and Incident Response
A robust incident response plan is critical to quickly detecting and responding to security incidents. Even with the best preventative measures in place, no system is immune to security threats.
- Monitoring: Real-time monitoring and logging help detect suspicious activity as it occurs. Set up automatic alerts for abnormal access patterns or data breaches so security teams can respond immediately.
- Incident Response Plan: An incident response plan outlines the steps to take when a security breach occurs. It includes isolating affected systems, mitigating damage, notifying stakeholders, and conducting a post-mortem to prevent future incidents. Regular drills and team exercises can help the team practice and improve response times.
Conclusion
Integrating security into the very fabric of custom software development is no longer optional – it’s a necessity. From encrypting sensitive data to implementing strong authentication protocols, every step of the development process should prioritise protecting the business and its users.
As cyber threats evolve, so must the security strategies used in custom software development. By following these best practices, companies can ensure that their custom software solutions remain secure, scalable, and resilient in an ever-changing threat landscape.