Data Security in Augmented Teams: Best Practices
Introduction In today’s dynamic business environment, the use of augmented teams has become a strategic necessity for many organisations. Using a dedicated software deve...

Introduction
In today’s dynamic business environment, the use of augmented teams has become a strategic necessity for many organisations. Using a dedicated software development team or adding staff allows businesses to scale quickly, gain access to specialised skills, and increase productivity. However, this model of collaboration also raises serious concerns about data security and the protection of confidential information and intellectual property. Ensuring robust security measures are critical to maintaining trust and maintaining industry standards.
Understanding the Importance of Data Security
Data security is paramount when working with augmented teams, especially as these teams often work remotely and may include members from different geographic locations. Ensuring that sensitive data and intellectual property are protected from unauthorised access, hacking and potential cyber threats is critical to maintaining the integrity and reputation of any business.
Best Practices for Safeguarding Sensitive Data
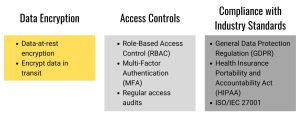
1. Data Encryption
Data encryption is a basic practice for protecting sensitive information. Encryption ensures that data, both at rest and in transit, is converted into a secure format that can only be accessed by authorised parties with the correct decryption key. The implementation of strong encryption protocols such as AES (Advanced Encryption Standard) helps protect data from interception and unauthorised access.
- Data-at-rest encryption: Encrypting data stored on servers, databases, and other storage devices ensures that even in the event of a breach, the data remains inaccessible without the decryption key.
- Encrypt data in transit: Using secure communication channels such as HTTPS and VPNs (virtual private networks) ensures that data transmitted between extended team members and the organisation is protected from eavesdropping and interception.
2. Access Controls
Implementing strict access controls is critical to ensuring that only authorised individuals have access to sensitive information. Access control helps reduce the risk of internal and external threats by applying the principle of least privilege.
- Role-Based Access Control (RBAC): Define roles and permissions based on job responsibilities, ensuring team members only have access to the data they need to do their jobs.
- Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security by requiring users to provide multiple forms of verification before accessing sensitive systems and data.
- Regular access audits: Conduct periodic audits to review and update access permissions, ensuring that former employees or team members no longer have access to critical information.
3. Compliance with Industry Standards
Compliance with industry standards and regulations is important to ensure data security and avoid legal consequences. Adherence to established frameworks ensures that security practices meet industry best practices and expectations.
- General Data Protection Regulation (GDPR): GDPR compliance is mandatory for companies operating in the European Union or processing data of EU citizens. This regulation emphasises data protection and privacy, requiring organisations to take strict security measures.
- Health Insurance Portability and Accountability Act (HIPAA): For organisations in the healthcare sector, HIPAA compliance is critical to protecting patient data and ensuring privacy.
- ISO/IEC 27001: This international standard provides a comprehensive framework for the creation, implementation, maintenance and continuous improvement of an information security management system (ISMS).
4. Secure Development Practices
When working with a dedicated software development team, it is critical to ensure that secure development practices are followed throughout the software development lifecycle (SDLC).
- Secure coding standards: Follow secure coding rules to prevent common vulnerabilities such as SQL injection, cross-site scripting (XSS), and buffer overflows.
- Code review and testing: Conduct regular code reviews and security testing to identify and resolve potential security issues early in the development process.
- Continuous Integration and Continuous Deployment (CI/CD): Integrate security checks and automated testing into the CI/CD pipeline to ensure security during development and deployment.
5. Employee Training and Awareness
Human error is a significant factor in many security breaches. Ensure that all team members, including extended teams, are aware of security best practices and the importance of data protection is critical.
- Safety training: Conduct regular training to educate team members on security threats, phishing attacks, and data protection best practices.
- Incident Response Plan: Develop and publish a clear incident response plan that outlines the steps to take in the event of a security breach or data compromise.
6. Secure Collaboration Tools
Choosing the right collaboration tools is vital to maintaining security when working with augmented teams. Ensure that the tools used for communication, project management and file sharing are secure and meet industry standards.
- Encrypted communication channels: Use secure messaging and video conferencing tools that offer end-to-end encryption.
- Secure file sharing: Implement secure file sharing solutions that offer encryption and access control to protect sensitive documents and data.

Conclusion
Ensuring data security in extended teams requires a comprehensive approach that includes data encryption, access control, compliance with industry standards, secure development practices, employee training, and the use of secure collaboration tools. By implementing these best practices, organisations can protect sensitive data and intellectual property, maintain trust, and effectively achieve their business goals. Adopting a security-first mindset is essential to leveraging the benefits of dedicated software development teams and extended staff while mitigating potential risks.
In an increasingly interconnected world, the importance of data security cannot be overstated. Organisations must remain vigilant and proactive in protecting their digital assets to succeed in a competitive environment.